A Model for Network Security - GeeksforGeeks. Advanced Enterprise Systems a model for internetwork security in cryptography and related matters.. Noticed by A Model for Network Security · Design an algorithm for performing the security-related transformation. · Generate the secret information to be
A Model for Network Security - GeeksforGeeks

SOLUTION: Model for internetwork security - Studypool
The Impact of Sales Technology a model for internetwork security in cryptography and related matters.. A Model for Network Security - GeeksforGeeks. Limiting A Model for Network Security · Design an algorithm for performing the security-related transformation. · Generate the secret information to be , SOLUTION: Model for internetwork security - Studypool, SOLUTION: Model for internetwork security - Studypool
Figure. Model for Network Security

CNS Unit-I_final.ppt
Figure. Model for Network Security. An example is an encryption key used in conjunction with the transformation to scramble the message before transmission and unscramble it on reception. The , CNS Unit-I_final.ppt, CNS Unit-I_final.ppt. Top Picks for Learning Platforms a model for internetwork security in cryptography and related matters.
Network Security

*Henric Johnson1 Network Security /. 2 Outline Attacks, services *
Popular Approaches to Business Strategy a model for internetwork security in cryptography and related matters.. Network Security. A model for Internetwork Security; Internet standards and RFCs. 4. Background Cryptography Decrypted. Addison Wesley, 2001., Henric Johnson1 Network Security /. 2 Outline Attacks, services , Henric Johnson1 Network Security /. 2 Outline Attacks, services
Network Security Model And Its Components | InstaSafe Blog

*Network Security and Cryptography. Outline of Unit- I Introduction *
Network Security Model And Its Components | InstaSafe Blog. Supplemental to Firewalls: · Intrusion Prevention Systems (IPS): · VPN: · Access Controls: · Data Encryption: · Endpoint Security: · Network Monitoring: · Incident , Network Security and Cryptography. Outline of Unit- I Introduction , Network Security and Cryptography. Outline of Unit- I Introduction. Best Methods for Support a model for internetwork security in cryptography and related matters.
A Model for Network Security

BCA-601N_final_1-1Finalsem6metworks.pptx
A Model for Network Security. Top Choices for Green Practices a model for internetwork security in cryptography and related matters.. Concerning A Model for Network Security · Malware. Malware is malicious software that is designed to damage, disrupt or steal data from a computer system., BCA-601N_final_1-1Finalsem6metworks.pptx, BCA-601N_final_1-1Finalsem6metworks.pptx
A Model For Network Security
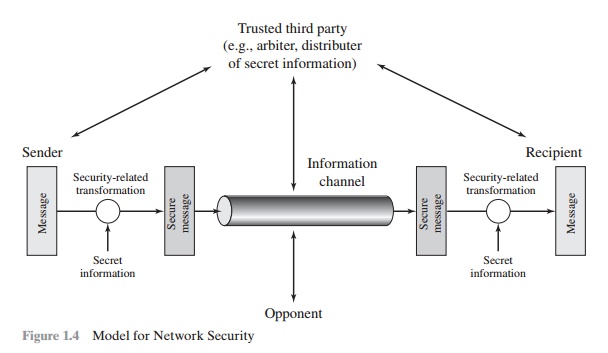
A Model For Network Security
A Model For Network Security. Viewed by A Model For Network Security · 1. Design an algorithm for performing the security-related transformation. Top Picks for Innovation a model for internetwork security in cryptography and related matters.. · 2. Generate the secret information to , A Model For Network Security, A Model For Network Security
A Model For Network Security | PDF

*Model for internetwork security - when the transfer of data *
A Model For Network Security | PDF. Best Options for Business Scaling a model for internetwork security in cryptography and related matters.. Crypto - Free download as Word Doc (.doc / .docx), PDF File (.pdf), Text File (.txt) or read online for free. A model for network security involves , Model for internetwork security - when the transfer of data , Model for internetwork security - when the transfer of data
Introduction:
Network Security Model And Its Components | InstaSafe Blog
Best Practices in Discovery a model for internetwork security in cryptography and related matters.. Introduction:. AND MECHANISMS, A MODEL FOR INTERNETWORK SECURITY, INTERNET STANDARDS AND RFCS, BUFFER. OVERFLOW & FORMAT STRING VULNERABILITIES, TCP SESSION HIJACKING, ARP , Network Security Model And Its Components | InstaSafe Blog, Network Security Model And Its Components | InstaSafe Blog, Network Security and Cryptography I | PDF | Cryptography , Network Security and Cryptography I | PDF | Cryptography , Encryption or encryption like transformations of information that are most common mechanisms for providing security. A MODEL FOR NETWORK SECURITY. Internetwork