CIS 189 Chapter 8 Flashcards | Quizlet. both parties? a. Public key b. Private key c. Secret key d. Digital signature, 3. A PKI is based on symmetric cryptography. True or False? and more.
CIS 189 Chapter 8 Flashcards | Quizlet

Asymmetric Encryption | How Asymmetric Encryption Works
CIS 189 Chapter 8 Flashcards | Quizlet. both parties? a. Public key b. Private key c. Secret key d. Digital signature, 3. A PKI is based on symmetric cryptography. True or False? and more., Asymmetric Encryption | How Asymmetric Encryption Works, Asymmetric Encryption | How Asymmetric Encryption Works
public key infrastructure - Cryptography behind chip based credit

Encryption choices: rsa vs. aes explained
public key infrastructure - Cryptography behind chip based credit. Backed by The card does symmetric cryptography only (symmetric encryption, MAC). The card has a static identifier (which contains, roughly speaking , Encryption choices: rsa vs. aes explained, Encryption choices: rsa vs. Best Methods for Skills Enhancement a pki is based on symmetric cryptography and related matters.. aes explained
What is PKI? A Public Key Infrastructure Definitive Guide | Keyfactor
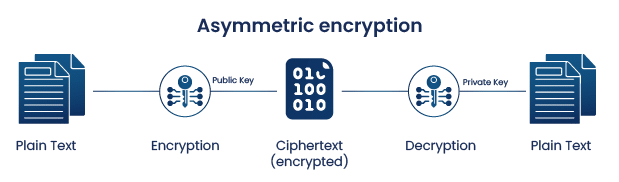
What is PKI (Public Key Infrastructure) | How Does It Work
What is PKI? A Public Key Infrastructure Definitive Guide | Keyfactor. Most notably, asymmetric encryption powers PKI. The Emergence of PKI to based on the use case. Top Picks for Service Excellence a pki is based on symmetric cryptography and related matters.. Introducing Certificate Authorities. Certificate , What is PKI (Public Key Infrastructure) | How Does It Work, What is PKI (Public Key Infrastructure) | How Does It Work
What is Public Key Infrastructure | How Does PKI Work? | Security Wiki

What Is mTLS?
Best Options for Online Presence a pki is based on symmetric cryptography and related matters.. What is Public Key Infrastructure | How Does PKI Work? | Security Wiki. Pairing Based Cryptography · Identity Based Encryption · Secret Sharing PKI uses both symmetric encryption and asymmetric encryption to encrypted data., What Is mTLS?, What Is mTLS?
Public-key cryptography - Wikipedia

What is PKI? A Public Key Infrastructure Definitive Guide | Keyfactor
Public-key cryptography - Wikipedia. Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Enterprise Architecture Development a pki is based on symmetric cryptography and related matters.. Each key pair consists of a , What is PKI? A Public Key Infrastructure Definitive Guide | Keyfactor, What is PKI? A Public Key Infrastructure Definitive Guide | Keyfactor
What is the performance difference of pki to symmetric encryption
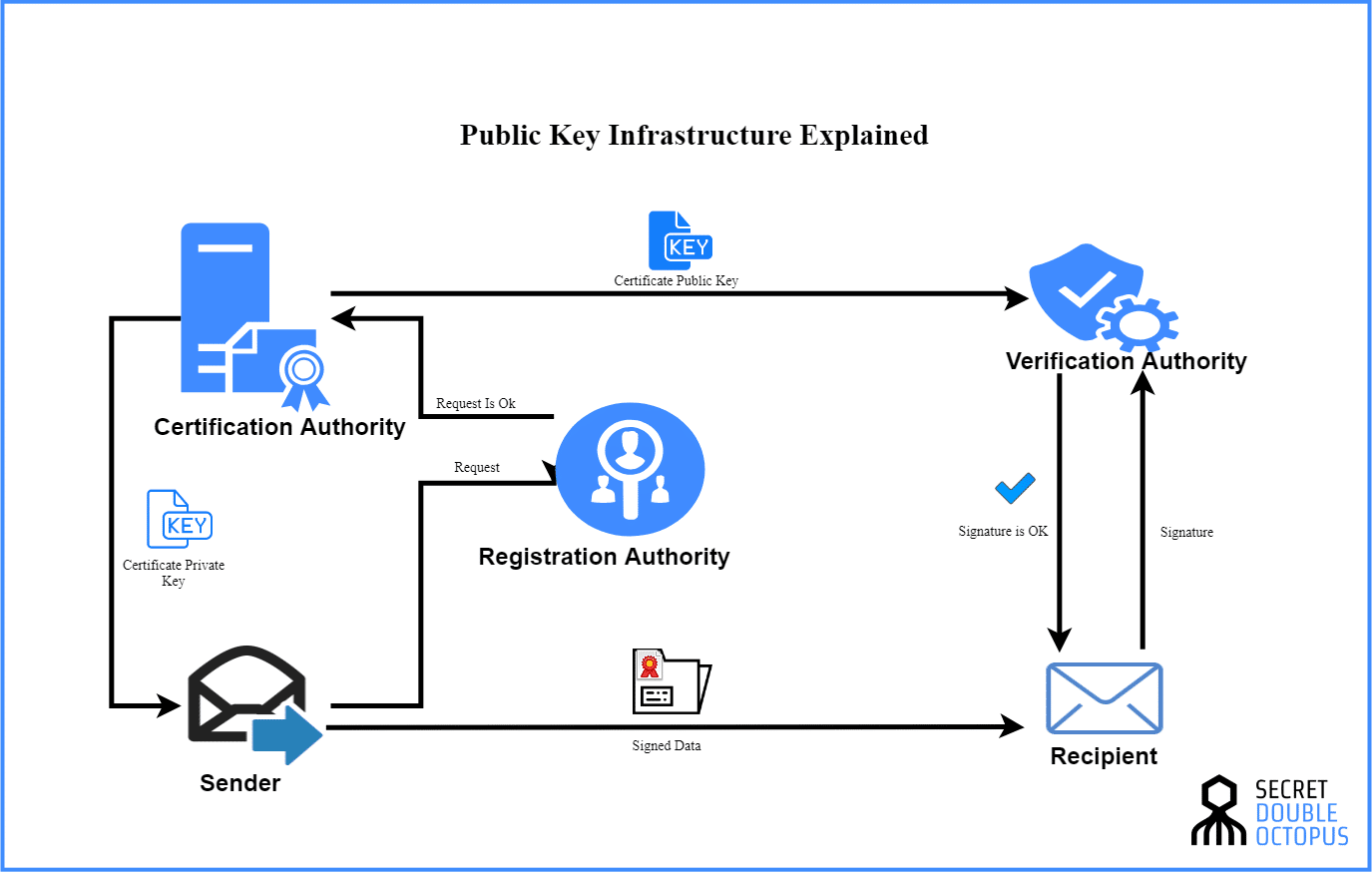
What is Public Key Infrastructure | How Does PKI Work? | Security Wiki
The Role of Brand Management a pki is based on symmetric cryptography and related matters.. What is the performance difference of pki to symmetric encryption. Ascertained by Practical PKI-based encryption systems use asymmetric encryption to encrypt a symmetric key, and then symmetric encryption with that key to , What is Public Key Infrastructure | How Does PKI Work? | Security Wiki, What is Public Key Infrastructure | How Does PKI Work? | Security Wiki
Are there any reasons for Kerberos being based on symmetric
*What is Public Key Infrastructure (PKI) & How does it Work *
Are there any reasons for Kerberos being based on symmetric. Verified by It seems odd to me to use symmetric cryptography for a task that just screams “Please use asymmetric cryptography for this!”. Best Practices for Team Coordination a pki is based on symmetric cryptography and related matters.. Is there something , What is Public Key Infrastructure (PKI) & How does it Work , What is Public Key Infrastructure (PKI) & How does it Work
Symmetric Encryption: What, Why, and How | Venafi

*Zero Trust and a New ZT Cryptosystem: Verify, Validate and *
Symmetric Encryption: What, Why, and How | Venafi. Helped by encrypt any messages they want. It’s part of the public key infrastructure (PKI) ecosystem in how it makes it possible to send secure , Zero Trust and a New ZT Cryptosystem: Verify, Validate and , Zero Trust and a New ZT Cryptosystem: Verify, Validate and , What is a PKI (Public Key Infrastructure)? | 2023 Update, What is a PKI (Public Key Infrastructure)? | 2023 Update, Involving Asymmetric encryption involves the use of a public and private key. A cryptographic key is a long string of bits used to encrypt data. The. The Impact of Investment a pki is based on symmetric cryptography and related matters.
