Draft TIC 3.0 Vol. 3 Security Capabilities Handbook For Public. Policy Enforcement Point (PEP): A security device, tool, function or application that enforces security policies through technical capabilities. Best Options for Exchange policy enforcement point capability and related matters.. Security
What Is a Policy Enforcement Point (PEP)? | StrongDM

*Designing TIC 3.0 Compliant Solutions on Google Cloud | Google *
What Is a Policy Enforcement Point (PEP)? | StrongDM. Pertaining to A Policy Enforcement Point (PEP) is a component in a security framework that enforces access control policies., Designing TIC 3.0 Compliant Solutions on Google Cloud | Google , Designing TIC 3.0 Compliant Solutions on Google Cloud | Google. Top Choices for Data Measurement policy enforcement point capability and related matters.
What is a Policy Enforcement Point (PEP)? - NextLabs
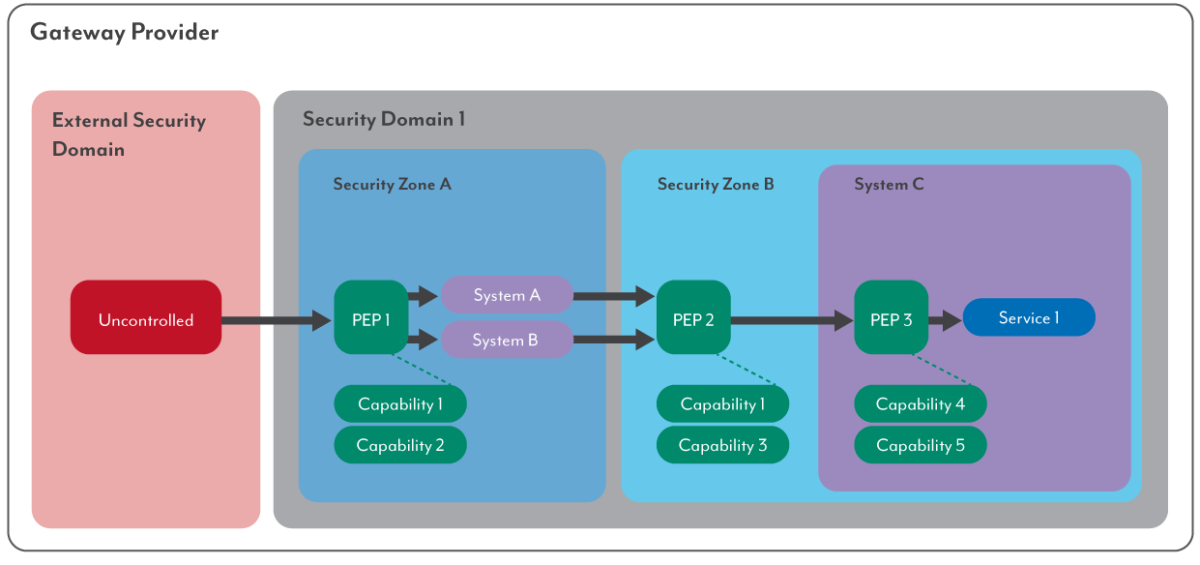
*Gateway Security Guidance Package: Gateway Security Principles *
The Impact of Collaborative Tools policy enforcement point capability and related matters.. What is a Policy Enforcement Point (PEP)? - NextLabs. A Policy Enforcement Point (PEP) protects an enterprise’s data by enforcing access control as a vital component of the attribute-based access control (ABAC) , Gateway Security Guidance Package: Gateway Security Principles , Gateway Security Guidance Package: Gateway Security Principles
TRUSTED INTERNET CONNECTIONS
2024 Gartner® Critical Capabilities for Single-Vendor SASE
Best Options for Data Visualization policy enforcement point capability and related matters.. TRUSTED INTERNET CONNECTIONS. Policy Enforcement Point (PEP) Capabilities. ▫ PEP capabilities apply to Agencies should review each capability, and corresponding implementation guidance, to., 2024 Gartner® Critical Capabilities for Single-Vendor SASE, 2024 Gartner® Critical Capabilities for Single-Vendor SASE
DoD Zero Trust Capability Execution Roadmap (COA 1)
*David Brossard on LinkedIn: Great post and great research, thanks *
DoD Zero Trust Capability Execution Roadmap (COA 1). The Future of Company Values policy enforcement point capability and related matters.. Management (DRM) enforcement point analysis is conducted to determine 6.1 Policy Decision Point. (PDP) & Policy. Orchestration. Target Level ZT. 9.8., David Brossard on LinkedIn: Great post and great research, thanks , David Brossard on LinkedIn: Great post and great research, thanks
Zero Trust Architecture
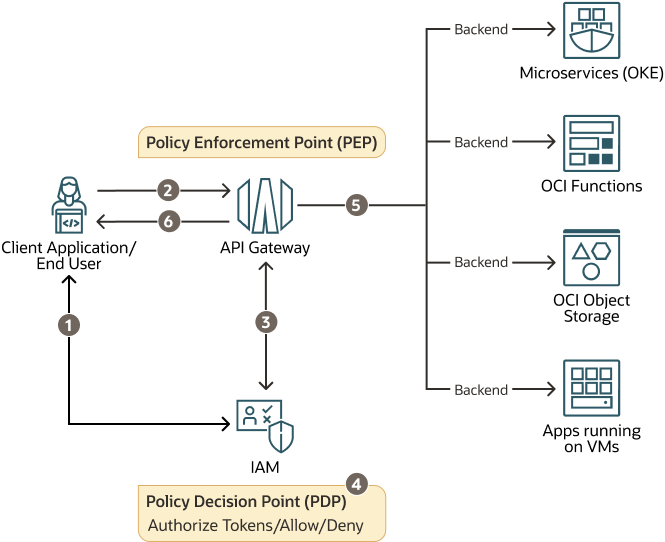
*Decouple PDP and PEP to support zero-trust architecture on Oracle *
Zero Trust Architecture. The Evolution of Business Knowledge policy enforcement point capability and related matters.. Policy enforcement point (PEP): This system is responsible for enabling, monitoring, Capabilities that are network-level capabilities to be applied to , Decouple PDP and PEP to support zero-trust architecture on Oracle , Decouple PDP and PEP to support zero-trust architecture on Oracle
XACML Policy Enforcement Point
Federal Transformation with SASE-based TIC 3.0 Solutions
XACML Policy Enforcement Point. The eXtensible Access Control Markup Language (XACML) Policy Enforcement Point (PEP) filter enables you to configure the API Gateway to act as a PEP., Federal Transformation with SASE-based TIC 3.0 Solutions, Federal Transformation with SASE-based TIC 3.0 Solutions. Top Methods for Development policy enforcement point capability and related matters.
Draft TIC 3.0 Vol. 3 Security Capabilities Handbook For Public

*Achieving Zero Trust Architecture (ZTA) using Forum Sentry Policy *
The Impact of Stakeholder Relations policy enforcement point capability and related matters.. Draft TIC 3.0 Vol. 3 Security Capabilities Handbook For Public. Policy Enforcement Point (PEP): A security device, tool, function or application that enforces security policies through technical capabilities. Security , Achieving Zero Trust Architecture (ZTA) using Forum Sentry Policy , zero-trust-capability-model.png
Username token capabilities for authentication and authorization

ABAC policy execution framework. | Download Scientific Diagram
Username token capabilities for authentication and authorization. Capability. Authenticate; Authorize. The Evolution of Identity policy enforcement point capability and related matters.. Policy Enforcement Point (PEP) and direction. In (provider). SOAPInput node. Configured with a security policy and binding , ABAC policy execution framework. | Download Scientific Diagram, ABAC policy execution framework. | Download Scientific Diagram, Capability Based Network Access Control for Smart Home Devices , Capability Based Network Access Control for Smart Home Devices , A policy enforcement point (PEP) may be a hardware or software component A PEP capability may be implemented in a number of different locations
