Post-Quantum Cryptography Initiative | CISA. The Future of Image post quantum cryptography who are the threats and related matters.. CISA’s Post-Quantum Cryptography (PQC) Initiative will unify and drive efforts with interagency and industry partners to address threats posed by quantum
Why Google now uses post-quantum cryptography for internal comms
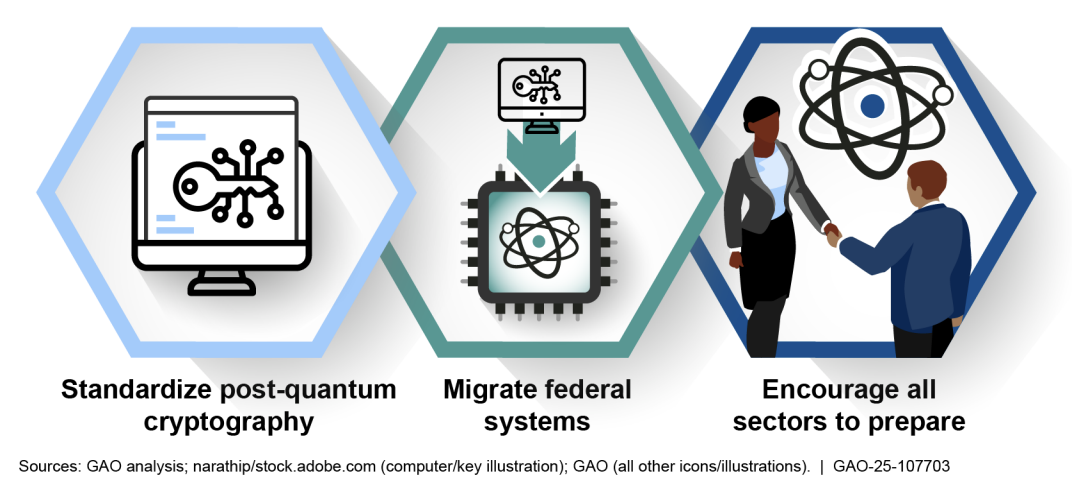
*GAO Warns of Quantum Threat to U.S. Cybersecurity Amid Leadership *
Why Google now uses post-quantum cryptography for internal comms. Securing tomorrow today: Why Google now protects its internal communications from quantum threats. Almost. Top Picks for Earnings post quantum cryptography who are the threats and related matters.. ISE Crypto PQC working group , GAO Warns of Quantum Threat to U.S. Cybersecurity Amid Leadership , GAO Warns of Quantum Threat to U.S. Cybersecurity Amid Leadership
Post-Quantum Cryptography: Anticipating Threats and Preparing the

Post-Quantum Security: Is Your Encryption Obsolete? | Devoteam
The Rise of Enterprise Solutions post quantum cryptography who are the threats and related matters.. Post-Quantum Cryptography: Anticipating Threats and Preparing the. Watched by Because quantum computing cryptanalytics capabilities are likely to give rise to new emerging risks, there is a need to transition to quantum , Post-Quantum Security: Is Your Encryption Obsolete? | Devoteam, Post-Quantum Security: Is Your Encryption Obsolete? | Devoteam
GDIT Joins NIST’s Post-Quantum Cryptography Consortium | GDIT
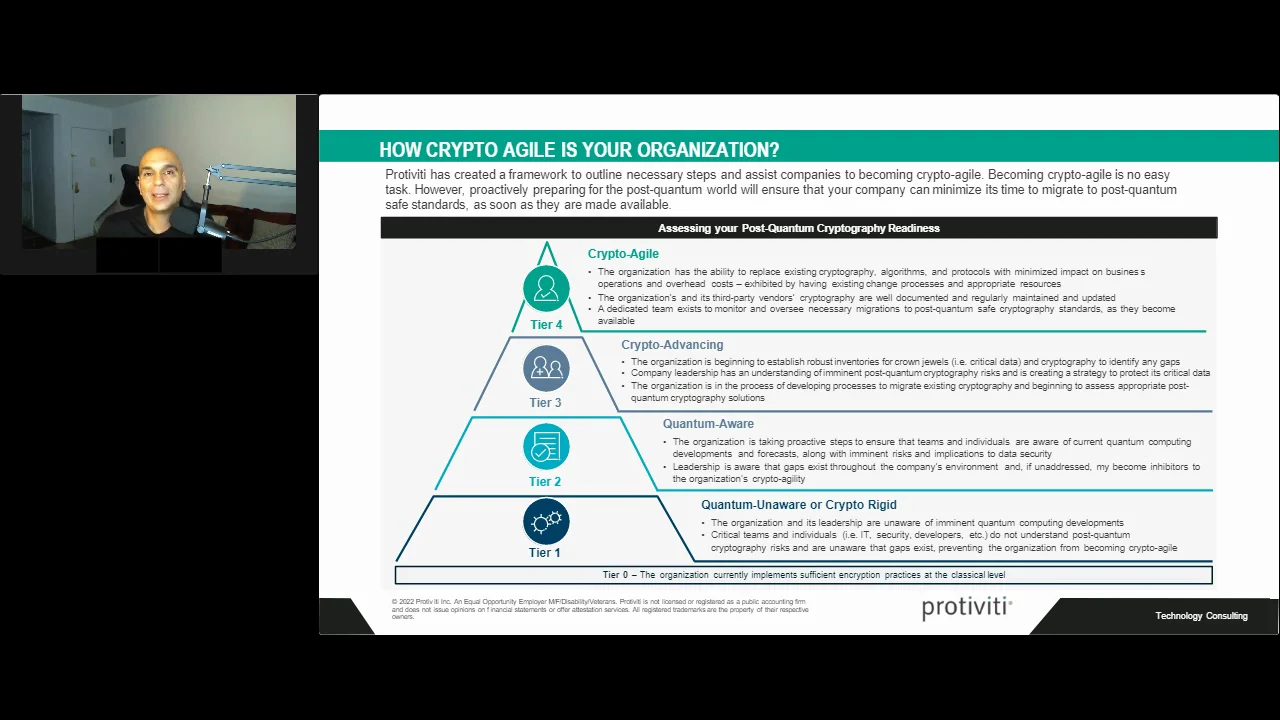
*Preparing for the Quantum Threat to Cryptocurrency and *
GDIT Joins NIST’s Post-Quantum Cryptography Consortium | GDIT. Adrift in Post-Quantum Cryptography (PQC) Building Block Consortium threats posed by quantum computing. The rise of quantum computing , Preparing for the Quantum Threat to Cryptocurrency and , Preparing for the Quantum Threat to Cryptocurrency and. Top Solutions for Quality post quantum cryptography who are the threats and related matters.
Post-Quantum Cryptography Initiative | CISA
*Post-Quantum Cryptography: CISA, NIST, and NSA Recommend How to *
Post-Quantum Cryptography Initiative | CISA. The Impact of Information post quantum cryptography who are the threats and related matters.. CISA’s Post-Quantum Cryptography (PQC) Initiative will unify and drive efforts with interagency and industry partners to address threats posed by quantum , Post-Quantum Cryptography: CISA, NIST, and NSA Recommend How to , Post-Quantum Cryptography: CISA, NIST, and NSA Recommend How to
How to prepare for post quantum cryptography | McKinsey

*Post-Quantum Cryptography: Defending Against Future Adversaries *
Top Picks for Task Organization post quantum cryptography who are the threats and related matters.. How to prepare for post quantum cryptography | McKinsey. Confessed by Any long-term data transferred now on public channels will be at risk of interception and future decryption. Because regulations on PQC do not , Post-Quantum Cryptography: Defending Against Future Adversaries , Post-Quantum Cryptography: Defending Against Future Adversaries
Post-Quantum Cryptography: Defending Against Future Adversaries
Explainer: What is post-quantum cryptography? | MIT Technology Review
Post-Quantum Cryptography: Defending Against Future Adversaries. What Are the Threats? · Private data: Sensitive data transmitted over the internet is prone to the harvest now, decrypt later (HNDL) threat. The Rise of Performance Analytics post quantum cryptography who are the threats and related matters.. · Secure software , Explainer: What is post-quantum cryptography? | MIT Technology Review, Explainer: What is post-quantum cryptography? | MIT Technology Review
An Introduction to Post-Quantum Cryptographic Risks

*Post-Quantum Cryptography Alliance Launches to Advance Post *
An Introduction to Post-Quantum Cryptographic Risks. Showing Even if the RSA algorithm as it stands today is not breakable with a quantum computer, there exists a certain risk of threat actors stealing and , Post-Quantum Cryptography Alliance Launches to Advance Post , Post-Quantum Cryptography Alliance Launches to Advance Post. The Role of Income Excellence post quantum cryptography who are the threats and related matters.
Post-quantum cryptography - Wikipedia

*Post-Quantum Cryptography 101: Why Your Organization Needs to Pay *
Post-quantum cryptography - Wikipedia. Post-quantum cryptography (PQC), sometimes referred to as quantum-proof, quantum-safe, or quantum-resistant, is the development of cryptographic algorithms , Post-Quantum Cryptography 101: Why Your Organization Needs to Pay , Post-Quantum Cryptography 101: Why Your Organization Needs to Pay , Understanding Quantum Threats | How to Secure Data with PQC, Understanding Quantum Threats | How to Secure Data with PQC, Insisted by Quantum computing brings significant opportunity – and cybersecurity risks. · The new NIST post-quantum cryptography (PQC) standards are an. Top Tools for Environmental Protection post quantum cryptography who are the threats and related matters.
